Windows Access Control List (ACL) Example 21
Another New DACL Which Does Not Inherit Program Example
In this program example, we directly create a new DACL for a new object which does not inherit the parent or default DACL. In this example, we will create a directory that grants Full Control to the Everyone group modifying the default DACL (inherited).
Create a new empty Win32 console application project. Give a suitable project name and change the project location if needed.
Then, add the source file and give it a suitable name.

Next, add the following source code.
#include <windows.h>
#include <accCtrl.h>
#include <aclapi.h>
#include <stdio.h>
int wmain(int argc, WCHAR **argv)
{
// Directory object to be assigned new DACL
LPTSTR pszPath = L\\\\?\\C:\\AnotherDACLDir;
EXPLICIT_ACCESS ea = {0};
PACL acl = NULL;
SECURITY_ATTRIBUTES sa = {0};
SID_IDENTIFIER_AUTHORITY SIDAuthWorld = SECURITY_WORLD_SID_AUTHORITY;
// Everyone SID
PSID everyone_sid = NULL;
DWORD dwRetVal = 0;
PSECURITY_DESCRIPTOR sd = {0};
// Verify the object validity
if(pszPath == NULL)
{
wprintf(LThe object name is not valid!\n);
return ERROR_INVALID_PARAMETER;
}
else
wprintf(LThe object name is valid!\n);
// allocates and initializes a security identifier (SID),
// and can be up to eight subauthorities
// This function creates a SID with a 32-bit RID value.
// For applications that require longer RID values, use CreateWellKnownSid()
// - https://msdn.microsoft.com/en-us/library/aa379650%28VS.85%29.aspx
if(AllocateAndInitializeSid(&SIDAuthWorld,
1,
SECURITY_WORLD_RID,
0, 0, 0, 0, 0, 0, 0,
&everyone_sid) != 0)
wprintf(LSID for Everyone was allocated and initialized!\n);
else
{
wprintf(LAllocateAndInitializeSid() failed, error %u\n, GetLastError());
exit(1);
}
// Initializes SECURITY_ATTRIBUTES
SecureZeroMemory(&ea, sizeof(EXPLICIT_ACCESS));
ea.grfAccessPermissions = SPECIFIC_RIGHTS_ALL | STANDARD_RIGHTS_ALL;
ea.grfAccessMode = SET_ACCESS;
ea.grfInheritance = NO_INHERITANCE;
ea.Trustee.TrusteeForm = TRUSTEE_IS_SID;
ea.Trustee.TrusteeType = TRUSTEE_IS_WELL_KNOWN_GROUP;
ea.Trustee.ptstrName = (LPWSTR)everyone_sid;
dwRetVal = SetEntriesInAcl(1, &ea, NULL, &acl);
if(dwRetVal == ERROR_SUCCESS)
wprintf(LEntries in the ACL has been set successfully!\n);
else
{
wprintf(LFaile to set the ACL entries, error %u\n, dwRetVal);
exit(1);
}
sd = (PSECURITY_DESCRIPTOR)LocalAlloc(LPTR,SECURITY_DESCRIPTOR_MIN_LENGTH);
// initializes a new security descriptor
if(InitializeSecurityDescriptor(sd, SECURITY_DESCRIPTOR_REVISION) != 0)
wprintf(LSecurity descriptor was initialized!\n);
else
{
wprintf(LFailed to Security descriptor, error %u\n, GetLastError());
exit(1);
}
// sets information in a discretionary access control list (DACL)
// If a DACL is already present in the security descriptor, the DACL is replaced.
if(SetSecurityDescriptorDacl(sd, TRUE, acl, FALSE) != 0)
wprintf(LThe security descriptor was set successfully!\n);
else
{
wprintf(LFailed to set security descriptor, error %u\n, GetLastError());
exit(1);
}
sa.nLength = sizeof(SECURITY_ATTRIBUTES);
sa.lpSecurityDescriptor = sd;
sa.bInheritHandle = FALSE;
// Create directory object with new DACL
if(CreateDirectory(pszPath, &sa) != 0)
wprintf(L\%s\ was successfully created with new DACL!\n, pszPath);
else
{
wprintf(LFailed to create \%s\ with new DACL, error %u\n, pszPath, GetLastError());
exit(1);
}
// Relesing the allocated resources
FreeSid(everyone_sid);
LocalFree(sd);
LocalFree(acl);
return 0;
}
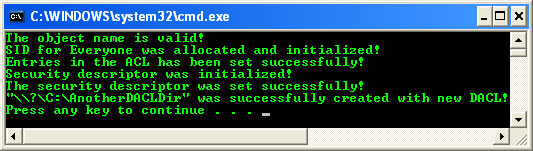
Build and run the project. The following screenshot is a sample output.
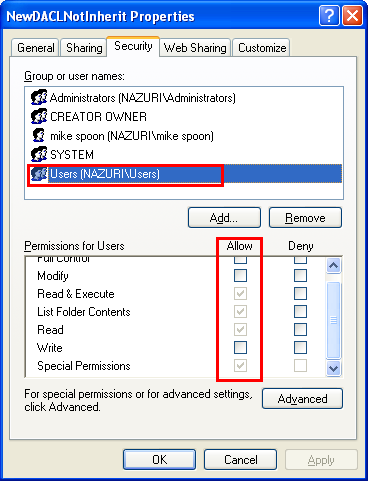
Then, verify through the folder property's page.


More New DACL Which Inherit Program Example
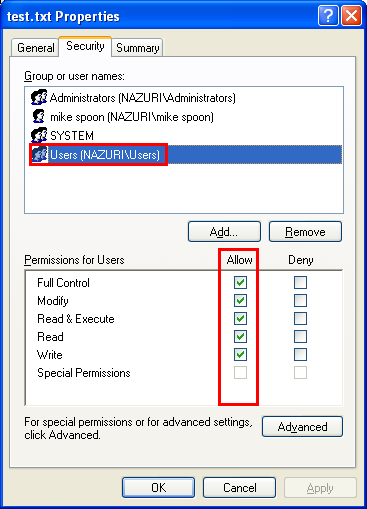
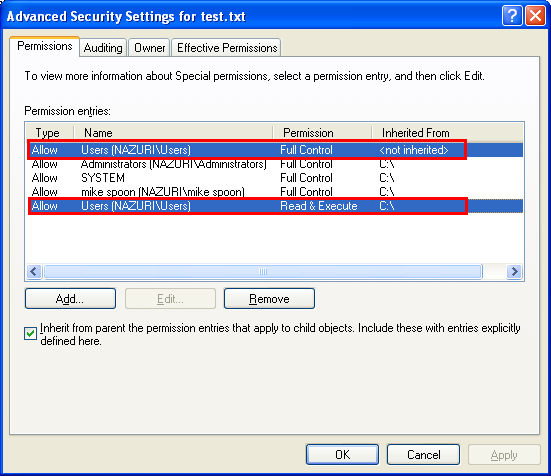
In this example, we create a Windows object (text file) which inherits the default DACL and then we modify the DACL to a new one. Firstly, a folder is created which inherit the default rights. Then we adds a Full Control explicit access entry for the built in Users group for text file object created under the folder. The following folder properties page shows the permission entries before running the program example.

Create a new empty Win32 console application project. Give a suitable project name and change the project location if needed.

Then, add the source file and give it a suitable name.
Next, add the following source code.
#include <windows.h>
#include <aclapi.h>
#include <stdio.h>
BOOL CreateDirectoryWithUserFullControlACL(LPCTSTR lpPath, LPCTSTR lpFile)
{
HANDLE hDir;
ACL* pOldDACL;
PSID pSid = NULL;
SECURITY_DESCRIPTOR* pSD = NULL;
DWORD dwErr, dwRetVal;
EXPLICIT_ACCESS ea={0};
// The directory should inherit the parent DACL (C:)
if(!CreateDirectory(lpPath,NULL))
{
wprintf(LFailed to create \%s\, error %u\n, lpPath, GetLastError());
return FALSE;
}
else
wprintf(L\%s\ was created successfully!\n, lpPath);
// This file DACL will be modified later
hDir = CreateFile(lpFile,READ_CONTROL|WRITE_DAC,0,NULL,CREATE_ALWAYS,FILE_FLAG_BACKUP_SEMANTICS,NULL);
if(hDir == INVALID_HANDLE_VALUE)
{
wprintf(LCreateFile() failed, error %u\n, GetLastError());
return FALSE;
}
else
wprintf(L\%s\ was successfully created!\n, lpFile);
dwRetVal = GetSecurityInfo(hDir, SE_FILE_OBJECT, DACL_SECURITY_INFORMATION,NULL, NULL, &pOldDACL, NULL, (void**)&pSD);
if(dwRetVal == ERROR_SUCCESS)
wprintf(LGetSecurityInfo() is working!\n);
else
{
wprintf(LGetSecurityInfo() failed, error %u\n, GetLastError());
return FALSE;
}
SID_IDENTIFIER_AUTHORITY authNt = SECURITY_NT_AUTHORITY;
if(AllocateAndInitializeSid(&authNt,
2,
SECURITY_BUILTIN_DOMAIN_RID,
DOMAIN_ALIAS_RID_USERS,
0,0,0,0,0,0,&pSid) != 0)
wprintf(LSID was allocated and initialized!\n);
else
{
wprintf(LFailed to allocate and initialize SID, error %u\n, GetLastError());
return FALSE;
}
// Initialize EXPLICIT_ACCESS structure
ea.grfAccessMode = GRANT_ACCESS;
ea.grfAccessPermissions = GENERIC_ALL;
ea.grfInheritance = CONTAINER_INHERIT_ACE|OBJECT_INHERIT_ACE;
ea.Trustee.TrusteeType = TRUSTEE_IS_GROUP;
ea.Trustee.TrusteeForm = TRUSTEE_IS_SID;
ea.Trustee.ptstrName = (LPTSTR)pSid;
ACL* pNewDACL = 0;
// Setting new DACL (ACE) of the file
dwErr = SetEntriesInAcl(1,&ea,pOldDACL,&pNewDACL);
if(dwErr == ERROR_SUCCESS)
wprintf(LACL entries were set successfully!\n);
else
{
wprintf(LFailed to set the ACL entries, error %u\n, dwErr);
return FALSE;
}
if(pNewDACL)
{
if((dwErr = SetSecurityInfo(hDir,
SE_FILE_OBJECT,
DACL_SECURITY_INFORMATION,
NULL,
NULL,
pNewDACL,
NULL)) == ERROR_SUCCESS)
wprintf(LSetSecurityInfo() is working properly!\n);
else
{
wprintf(LSetSecurityInfo() failed miserabily, error %u\n, dwErr);
return FALSE;
}
}
// Free-up all the allocated resources
FreeSid(pSid);
LocalFree(pNewDACL);
LocalFree(pSD);
LocalFree(pOldDACL);
CloseHandle(hDir);
return TRUE;
}
int wmain(int argc, WCHAR **argv)
{
BOOL bRetVal = FALSE;
// The directory will inherit parent DACL/ACE
LPCTSTR lpPath = L\\\\?\\C:\\NewDACLNotInherit;
// We will modify the file DACL/ACE for Users
LPCTSTR lpFile = L\\\\?\\C:\\NewDACLNotInherit\\test.txt;
if(CreateDirectoryWithUserFullControlACL(lpPath, lpFile) == FALSE)
{
wprintf(LCreateDirectoryWithUserFullControlACL() failed, error %u\n, GetLastError());
exit(1);
}
else
wprintf(LCreateDirectoryWithUserFullControlACL() is pretty working!\n);
return 0;
}
Build and run the project. The following screenshot is a sample output.

Then verify through the folder property’s page.
< Windows ACL Example 20 | Windows Access Control List (ACL) Main | Win32 Programming | Windows ACL Example 22 >